Auto Makers’ Strategy of Turning Cars into Four-wheel Smartphones will Bring Enterprise Security into Focus

About 80% of the new generations of automobiles will be connected to the internet by 2017, from 25 percent already, CEOs have started speaking publicly about smart cars, and developers admit the security challenges facing the new market.
“As IT&C research and technologies develop exponentially, the way we work will change dramatically because customers want the latest technologies in their cars so the rhythm of introducing breakthrough features in our products will be much faster”, said Jean Christophe Kugler, Renault’s Senior Vice President and President of the Board for Eurasia to the media at the 2015 Frankfurt Motor Show this autumn.
Recent studies show electronic components now make up over 50% of the manufacturing cost of a car, with some cars now containing over 100 million lines of code,a clear source of worrisome security vulnerabilities.
„The automotive industry permanently changes and what used to amaze the day before now does not impress anymore. Customers do not choose cars only by looking to features such as design, power or torque, but also technology. By the end of the decade, we will launch up to 20 new models of electric and hybrid cars, and in the same period every new car available for sale will act as a four-wheel smartphone “, added Martin Winterkorn, former chairman of Volkswagen AG and president of the German Automotive Industry Association (VDA). VDA’s 600 members, including Daimler AG, Bayerische Motoren Verke AG and Volkswagen AG, will invest 16 billion to 18 billion euros in the next 3-4 years in R&D for connected and fully automated cars.
According to researchers from Ponemon Institute, estimates are that 60-70% of vehicle recalls are due to software glitches. Cars are run by networks of computers, wireless connections and electronic control units (ECUs), offering the potential for hackers to access critical car controls, including steering and braking. Modern cars can easily connect to smart devices and the internet. This could expose critical systems to hackers, leading to remote attacks on cruise control mechanisms, braking systems, and other safety-critical operations, compromising automakers’ both credibility and business forecasts.
More than 500 people directly involved in developing automotive software answered a recent survey, with nearly 80% coming from OEMs and Tier One suppliers. Some 44% of the developers surveyed believe hackers are actively targeting automobiles. This demonstrates that developers are aware of the security and safety vulnerabilities that their code could present, even if the possibility is remote.
Despite the understanding that automobiles are hacking targets, only 41% of developers polled agree (and 28% disagree) that secure software is a priority for their company. Worse, 69% believe that securing the applications is difficult/very difficult and nearly half (48%) believe a major overhaul of the car’s architecture is required to make it more secure. Only 19% think it is even possible to make a car “nearly hack proof.”
Identifying barriers to security is paramount, researchers say. To some extent, those on the automotive supply chain have not considered themselves “in the software business” until recently, when hacks and threats began flooding the media. For this reason, only 28% of those polled believe that automakers are as knowledgeable about secure software development as are other industries. Not only is basic knowledge a barrier, but training is also insufficient. Less than half of the automotive software developers believe they are adequately trained in secure architecture and coding practices. Even though they acknowledge the gaps, they still have the responsibility to avoid life-threatening security failures.
“The transportation industry has traditionally been very reluctant to working with security researching for finding potential vulnerabilities. But, as it turns out, researchers have uncovered a number of issues with firmware deployed on various models that could threaten the safety of passengers,” says Bogdan Botezatu, Bitdefender’s Senior eThreat Analyst. “As these vehicles get more and more interconnected, closer collaboration between car manufacturers and the security research community would dramatically help the former iron out potential bugs and make transportation more secure. Let’s not forget that cars are consumer goods with a very long exploitation lifespan and a car that ships with software vulnerabilities will likely remain vulnerable until it’s recycled.”
Yet the lack of knowledge on how to move forward doesn’t mean that automakers are doing nothing to secure their applications. As the Car Cybersecurity study shows, 63% are running automated software scans during development, half are scanning after the application has been released, and 36% are conducting penetration tests. But only a quarter of those surveyed say they adhere to secure coding standards or conduct high-level assessments, such as threat models. They also realize they will need a change in software development processes as well as specially trained staff to improve security in automobiles. The key will be for the companies to begin operating and behaving like software companies, using the proven and tested methods of others to avoid reinventing the wheel, but at the same time making a major shift in their standard operating procedures.
Experts say that, fundamentally, companies should be making it easier for developers to create secure code. Companies need their developers to focus on innovation, and not tedious processes for ensuring security. Providing processes, policies and tools makes security non-negotiable. Security should be infused in every step of the systems’ development life cycle, but only 45% of developers indicate their development processes include any activity that supports security requirements. The majority of the respondents believe the CIO was the person most responsible for security in their organization – but that role rarely, if ever, even touches the code.
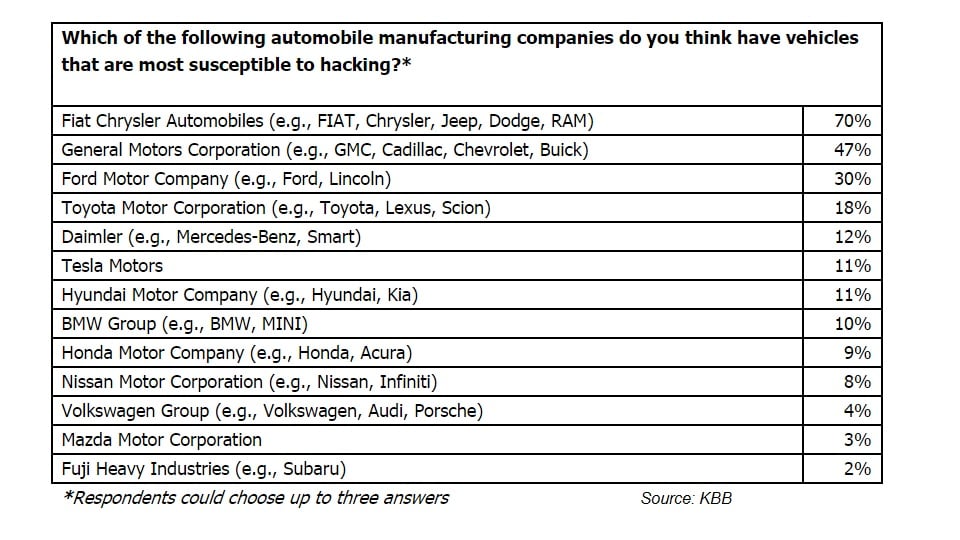
Potential vulnerabilities in smart cars and all the safety challenges that result have raised drivers’ awareness of the risks of someone else taking control of their cars while driving. Some 52 percent would pay a monthly subscription to ensure their vehicle is completely protected from hacking, with $8 being the average amount paid each month, according to the Vehicle Hacking Vulnerability Survey by Kelley Blue Book.
Nearly 80% say car hacking will be a common problem within three years, the study authors found. Some 58% think there will never be a permanent solution to vehicle hacking. About 41% think pranking is the most common reason to hack a vehicle, and 37% think theft is the most common. More than 80% think the manufacturer is most responsible to secure a vehicle from hacking, and most would prefer a security patch installed at a dealership right away, the study shows. Only 11% consider themselves most responsible for securing a vehicle from hacking, and 5% see it as the responsibility of their wireless provider.
Besides customer requirements, The Security and Privacy in Your Car (SPY) Act of 2015 proposed in the US Senate this summer could also force automakers to update software more, isolate critical systems from the car’s internal network and clearly state data collection practices. The new privacy standards, to be developed by the National Highway Traffic Safety Administration (NHTSA), will require automakers to tell car owners what data is being collected, transmitted and shared.
“All entry points to the 23 electronic systems of each motor vehicle manufactured for sale in the United States shall be equipped with reasonable measures to protect against hacking attacks. Each motor vehicle shall provide clear and conspicuous notice, in clear and plain language, to the owners or lessees of such vehicle of the collection, transmission, retention, and use of driving data collected from such motor vehicle,” the paper says. European authorities plan taking similar measures in the upcoming months.
Automakers and suppliers will have to adapt their hardware and software architectures, their code and their processes to deal with this new threat to automobiles, yet OEMs don't have the skills, tools or processes to make a secure car, as studies show. Customers ask for security, and would even pay for it. And governments want to make it mandatory. So it is quite obvious why cyber security professionals have put this on the board’s top priorities.
{{cta('1f813eca-ccf8-4f3d-9b9b-ce16c1139d23','justifycenter')}}
tags
Author

Former business journalist, Razvan is passionate about supporting SMEs into building communities and exchanging knowledge on entrepreneurship. He enjoys having innovative approaches on hot topics and thinks that the massive amount of information that attacks us on a daily basis via TV and internet makes us less informed than we even think. The lack of relevance is the main issue in nowadays environment so he plans to emphasize real news on Bitdefender blogs.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks







