Understanding and Managing Software Vulnerabilities: A Comprehensive Guide

In June 2023, a significant cybersecurity incident sent shockwaves through the corporate world. The CL0P hacker group exploited a vulnerability in MOVEit software, leading to severe data breaches. CL0P targeted organizations like banks, federal agencies, and corporate entities. This is a stark reminder of the importance of understanding and managing vulnerabilities in the evolving realm of cybersecurity. If unchecked and exploited, these vulnerabilities lead to significant security breaches, compromising sensitive data, disrupting critical processes, and causing severe damage to an organization. This guide aims to shed light on vulnerability management, the process of reporting and assessing vulnerabilities, and the tools available for remediating Common Vulnerabilities and Exposures (CVEs).
Unraveling the Terminology
Cybersecurity terminology can be daunting, especially when understanding the differences between similar-sounding terms. Two such terms that often cause confusion are 'weakness' and 'vulnerability'.
In cybersecurity, a vulnerability is defined as a weakness in automated system security procedures, administrative controls, internal controls, and/or an IT system, which could be exploited by a threat to gain unauthorized access to information or disrupt critical processing. This definition, provided by the National Information Assurance Training and Education Center, underscores the fact that vulnerabilities can affect not only software and hardware but also the procedures and controls set in place by an organization.
On the other hand, a weakness can lead to vulnerabilities, but if there is no way to exploit a weakness, it's just that — a weakness. A vulnerability is a weakness that can be actively exploited. This distinction is crucial because it highlights the fact that not all weaknesses pose a threat. However, when a weakness can be actively exploited, it becomes a vulnerability, posing a potential risk to the system's security.
Another term that is central to understanding vulnerability management is Common Vulnerabilities and Exposures (CVE). This is a system of referencing publicly known information-security vulnerabilities and exposures. It's both a standardized designation and dictionary, providing a universally accepted way of naming and organizing known vulnerabilities. The system is maintained by The MITRE Corporation, with funding from the National Cyber Security Division of the U.S. Department of Homeland Security, and was officially launched for the public in September 1999.
Reporting and Assessing Vulnerabilities
The process of reporting and assessing vulnerabilities is a critical aspect of vulnerability management. If a vulnerability is found by a malicious actor in a system, it can be exploited indefinitely until it’s detected, reported, and (hopefully) remediated. This highlights the importance of robust vulnerability detection and reporting mechanisms.
The Open Web Application Security Project (OWASP) provides a handy cheat sheet for guidance on the commonly accepted vulnerability disclosure process. This process includes having a system in place to internally report vulnerabilities, along with a triage/assign/fix process, and a system to report vulnerabilities to external audiences, again with a triage/assign/fix process.
The severity of a vulnerability is determined using the Common Vulnerability Scoring System (CVSS), which is a free and open standard. It quantitatively assesses computer system security vulnerabilities using Base, Temporal, and Environmental Metrics. Base Metrics focus on the intrinsic aspects of a vulnerability, such as the Attack Vector (AV), Attack Complexity (AC), Privileges Required (PR), User Interaction (UI), Scope (S), and impacts on Confidentiality (C), Integrity (I), and Availability (A) of the system. Temporal Metrics change over time and include Exploitability (E), Remediation Level (RL), and Report Confidence (RC), reflecting the state of exploit techniques, available fixes, and the credibility of the vulnerability report. Environmental Metrics are customized per user environment, reflecting the impact within the specific context. The final CVSS score ranges from 0.0 (no vulnerability) to 10.0 (critical vulnerability), aiding organizations in prioritizing their security efforts.
Tools for Remediating CVEs
In the battle against cyber threats, having the right tools at your disposal is crucial. Here are some of the available tools, each with its strengths and limitations:
Configuration Management Databases (CMDB)
These databases serve as the central repository of information about an organization's assets — software, hardware, systems, products, and even people — and the relationships among all those assets. While CMDBs are excellent at asset management and configuration tracking, they don’t provide much visibility into the network or connections being made with other assets that may appear unaffected at the surface.
Cloud Security Tools
Tools like Cloud Access Security Brokers (CASBs), Cloud Security Posture Management (CSPM) tools, Cloud Workload Protection Platforms (CWPPs), and Cloud-Native Application Protection Platforms (CNAPPs) have become increasingly important as more organizations move their operations to the cloud. However, their scope is limited, and they do not provide comprehensive protection for on-premises systems or underlying infrastructure.
Patch Management Solutions
Patch management solutions are essential cybersecurity tools that help organizations keep their software, operating systems, and applications updated, thereby reducing vulnerabilities, enhancing system security, and ensuring compliance with key regulations, ultimately protecting businesses from potential cyber threats and data breaches.
One example of such a solution is Bitdefender's GravityZone Patch Management add-on. It is a comprehensive cybersecurity solution that automates patch application to address system vulnerabilities from outdated software and applications. It enhances security, simplifies IT processes, and provides a complete view of patch status across Windows and Linux infrastructure. Offering both manual and automatic patching, it ensures regulatory compliance and reduces the risk of security breaches by addressing unpatched vulnerabilities, serving as a proactive defense against advanced cyber threats.
Vulnerability Scanners
Vulnerability scanners are vital tools for cybersecurity professionals that assist in identifying and evaluating potential weaknesses in a system's security. Nessus, developed by Tenable Network Security, is renowned for its thoroughness and accuracy in detecting vulnerabilities across a wide variety of systems, including networks, devices, operating systems, applications, databases, and more. It offers comprehensive reporting, compliance checks, and patch management capabilities, making it a robust solution for vulnerability management. On the other hand, Shodan is a unique scanner often referred to as the "search engine for the Internet of Things (IoT)". Unlike traditional vulnerability scanners, Shodan scans the entire internet and provides information about all types of connected devices, from servers and routers to security cameras and smart TVs. Shodan aids in uncovering exposed systems and ports, thus helping to reveal potential attack vectors. Both Nessus and Shodan, albeit different in their approaches, play critical roles in proactively identifying vulnerabilities and strengthening the overall security posture of an organization or network.
Organizations looking to consolidate their vulnerability scanning with their cybersecurity may also consider Bitdefender GravityZone, which includes a powerful user, system, and application risk assessment tool. The tool allows security teams to scan for, and identify risks associated with the Windows and Linux Operating Systems misconfigurations, vulnerable applications, and human-based behavior that could put organizations at risk from security breaches.
Just as a food ingredient list gives us insight into what we're consuming, a Software Bill of Materials (SBOM) provides crucial information about the components that make up our software. It's a formal record of the exact versions of the software components used in an application. For businesses and users, this is a crucial tool that aids in vulnerability management. Notably, it allows the user to understand whether any part of the software they are using is vulnerable and requires remediation or updating, helping to reduce the probability of a software supply chain attack.
In case of a security incident, an SBOM facilitates rapid identification of affected systems, aiding in reducing the attack impact. It assists with compliance checks to meet licensing requirements and regulations, reducing legal risks. Moreover, it aids in risk analysis, allowing organizations to make informed security decisions. In the context of supply chain attacks, SBOMs provide insights into potential risks from third-party software components. If a component is compromised, organizations can rapidly gauge the impact and act, limiting the potential damage from such an attack.
Predictive CVE Monitoring
In the constantly evolving world of cybersecurity, waiting for a security threat to occur before responding is no longer enough. It's like trying to put out a fire after it has engulfed an entire forest. Wouldn't it be better if we could predict where the fire might start, enabling us to prevent it altogether?
To help with the predictions, Bitdefender MDR’s Cyber Intelligence Fusion Cell (CIFC) has been developing processes to attempt to stay ahead of threats. CIFC uses open-source information and sifts through mountains of data to identify and monitor trending CVEs (seen below, in Figure 1), which can help the MDR team stay aware of possible exploits and conduct threat hunting to identify potential cyber threats.
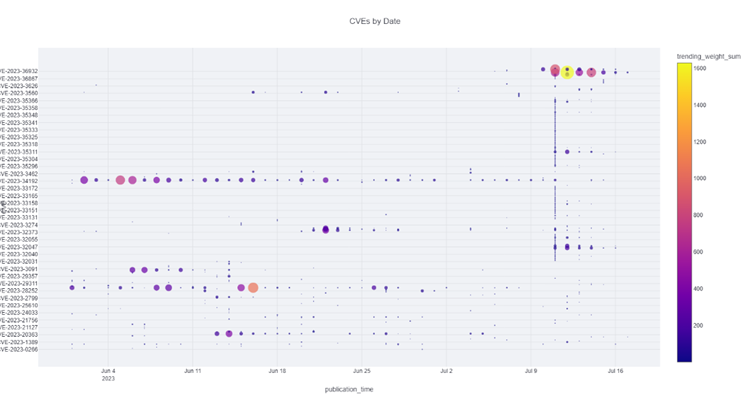 Figure 1: CVE trends over one week
Figure 1: CVE trends over one week
By focusing on likely threats rather than reacting to every potential vulnerability, organizations can optimize their resources, saving both time and money while still achieving optimal levels of cybersecurity.
Indeed, cybersecurity is no longer just about defense; it's about foresight, anticipation, and proactive action. As we can see with the recent Microsoft vulnerability (CVE-2023-36884) that allowed remote code execution (RCE) in Figure 2 below, our monitoring allows us to see when the first research or news stories are published, as well as over time gaining additional reference sources and context to help with the team’s assessment and analysis.
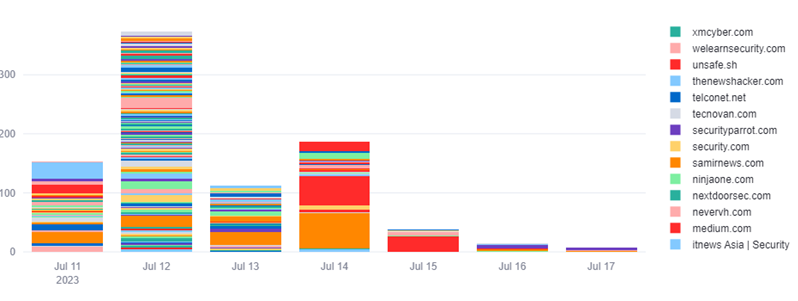
Figure 2: CVE-2023-36884 references over approximately one week
With a more proactive approach, we're striving to stay ahead of threats rather than merely responding to them. As the cyber threat landscape continues to evolve, we stand ready to meet these challenges head-on, always prioritizing the security of our customers.
Moving Forward
Given the complex landscape of software vulnerabilities, it’s essential for organizations to adopt robust vulnerability management strategies. It's not just about having the right tools, but also about understanding the landscape of vulnerabilities and making informed decisions. As we move forward in this increasingly connected world, let's strive to better understand and manage software vulnerabilities, thereby helping ensure a more secure future.
Learn More About Bitdefender Managed Detection and Response.
tags
Author
Bitdefender is a cybersecurity leader delivering best-in-class threat prevention, detection, and response solutions worldwide. Guardian over millions of consumer, enterprise, and government environments, Bitdefender is one of the industry’s most trusted experts for eliminating threats, protecting privacy, digital identity and data, and enabling cyber resilience. With deep investments in research and development, Bitdefender Labs discovers hundreds of new threats each minute and validates billions of threat queries daily. The company has pioneered breakthrough innovations in antimalware, IoT security, behavioral analytics, and artificial intelligence and its technology is licensed by more than 180 of the world’s most recognized technology brands. Founded in 2001, Bitdefender has customers in 170+ countries with offices around the world.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks








