If you’re running a company you might like to imagine that all of your staff are happy in their positions, feeling fulfilled by the career opportunities that you have provided to them, and content imagining a future where they will always be working for your firm.
The reality, however, is different.
However great you imagine the working environment is that you provide for your staff, chances are that some of your employees are beginning to consider seeking employment elsewhere.
And it’s precisely that temptation of a new job which online criminals are exploiting in a new malware campaign launched via LinkedIn.
Security researchers at Proofpoint report that potential victims at US businesses are receiving messages via LinkedIn’s direct messaging system that pretend to come from a company with an offer of employment.
To appear more convincing, the attackers have created fraudulent LinkedIn profiles for themselves, backed up with bogus websites posing as a legitimate recruitment agency.
Initially the attacker sends a harmless-looking “please add me to your professional network” connection request to their targeted victim, with mention that they are recruiting for a similar (but better paid) position at a nearby firm.

According to the researchers, within a week the attacker sends personalised email directly to their intended victim’s business email address following up on the LinkedIn conversation. To appear more convincing, the email will refer to the target’s current job title in the subject line and message body when describing the new opportunity.
The email invites the recipient click on a link to read more about the fictional job opportunity.
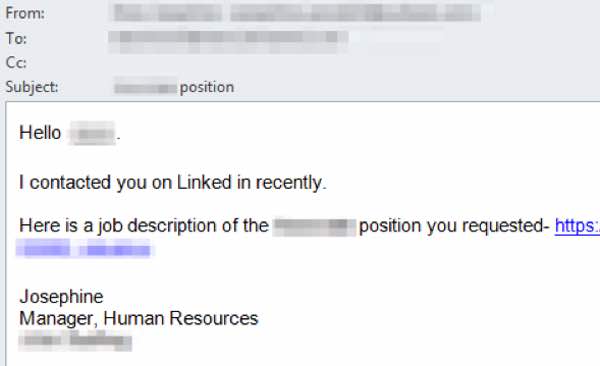
In other cases the email may not be accompanied by a link, but a boobytrapped file attachment containing malicious URLs.
The end result is the same, however. If the targeted individual visits the dangerous URL they visit the bogus recruitment site, and a Microsoft Word file containing malicious macros is downloaded.
The intended victim is told to click on “Enable Content” button to view the document’s content, ignoring the security warning built into Microsoft Word.
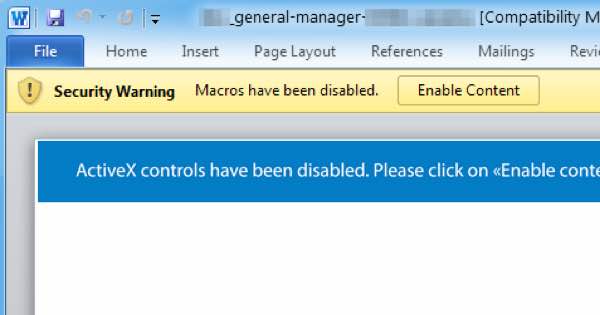
Of course, a person who is curious about a new job opportunity paying a higher salary is more likely to click on links and allow macros to run in the Word document than a user who has not been duped into believing that they are talking to a genuine recruiter.
What gets installed onto victims’ computers is a version of the More_eggs backdoor trojan, which can be used to download further malware onto a computer or open a backdoor for a hacker to gain remote access to the business’s network.
Although technology can help defend against attacks like this reaching your staff, it’s always a better defence to raise awareness amongst your workforce and train them in how to use their business computers more safely.
For instance, staff should be taught to be wary of clicking on links or open attachments in unexpected emails. And, of course, enabling macros in a Word document is asking for trouble.
If you’re ever in doubt, check with your IT department to see if an email or link is safe to click on. I understand that that might be difficult if the email is specifically about a new job at a different company, but hey… it doesn’t ever do you any harm to make a good buddy you can trust in the IT support team.
And, if you do think you may have made a mistake and clicked on a link you shouldn’t have, or opened a file that you perhaps shouldn’t have trusted… always inform your IT team. They would much rather know that there is a potential problem than have it brushed under the carpet, potentially causing a much bigger security incident.






