On April 11, 2023, Microsoft released a patch for a vulnerability in Microsoft Message Queuing (MSMQ) service. CVE-2023-21554 (dubbed QueueJumper) is a critical unauthorized remote code execution (RCE) vulnerability with a CVSS score of 9.8. Attack complexity is low, and it doesn’t require any privileges or user interaction. To exploit this vulnerability, threat actors would send a malicious MSMQ packet to a listening MSMQ service.
What is MSMQ?
Microsoft Message Queueing is a technology that enables asynchronous communication between applications. It decouples sending and receiving components of a distributed system, making it a popular choice when designing applications that can support heterogenous networks and offline usage. While MSMQ can be considered a legacy technology, it is available on a wide range of Microsoft operating systems, including the latest build of Windows 11. MSMQ was commonly used as a middleware component of enterprise applications and is fully integrated with Microsoft’s .NET Framework.
Any vulnerability in a middleware component can have a cascading effect on other systems. We are releasing this technical advisory to help our customers identify potentially vulnerable systems and take proactive steps to mitigate this vulnerability. As of the writing of this advisory, there is no public proof of concept (POC) exploit available, and no actual incidents have been reported.
Recommendations
It is strongly recommended to install Microsoft's official patch as soon as possible for this vulnerability. Legacy enterprise applications are often subject to delayed or skipped patches, but doing so can result in significant consequences. It is important to prioritize patching for systems that are accessible from the internet, but it is equally important not to overlook the need to patch internal-only systems. We have previously documented the rising trend of weaponizing newly discovered vulnerabilities and opportunistic attacks, and this latest vulnerability has all the attributes that threat actors are looking for. Read more about GravityZone Patch Management to keep your systems up to date.
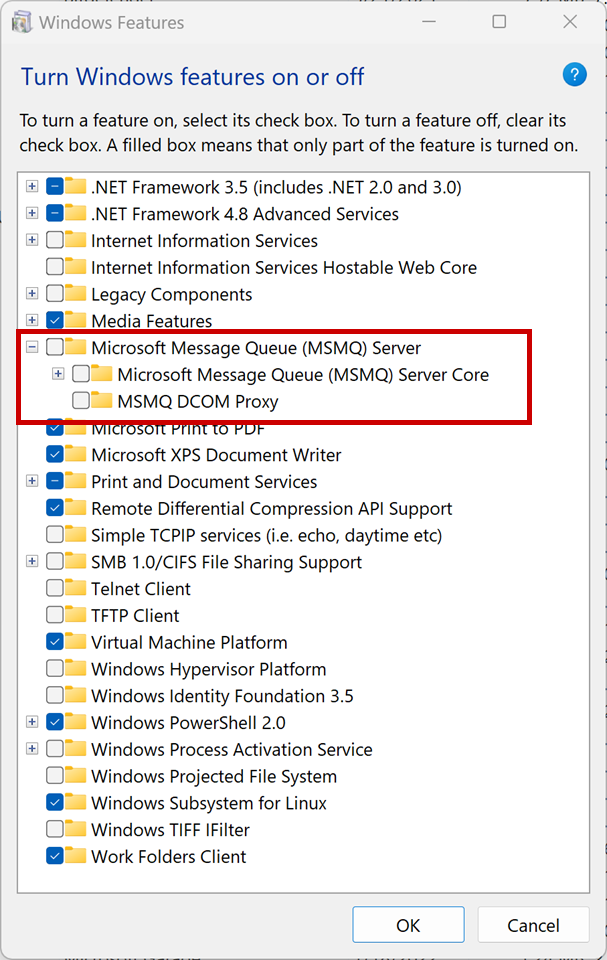
Conduct an extensive infrastructure and software application audit to identify all systems where MSMQ is being deployed. To locate the vulnerable versions of MSMQ service in your environment, use the Live Search query feature of the GravityZone platform. With Live Search, you can retrieve information about events and system statistics directly from online endpoints using OSquery, an operating system instrumentation framework that uses the SQLite query language. This is currently available for customers that have enrolled in the Early Access program available in GravityZone Cloud.
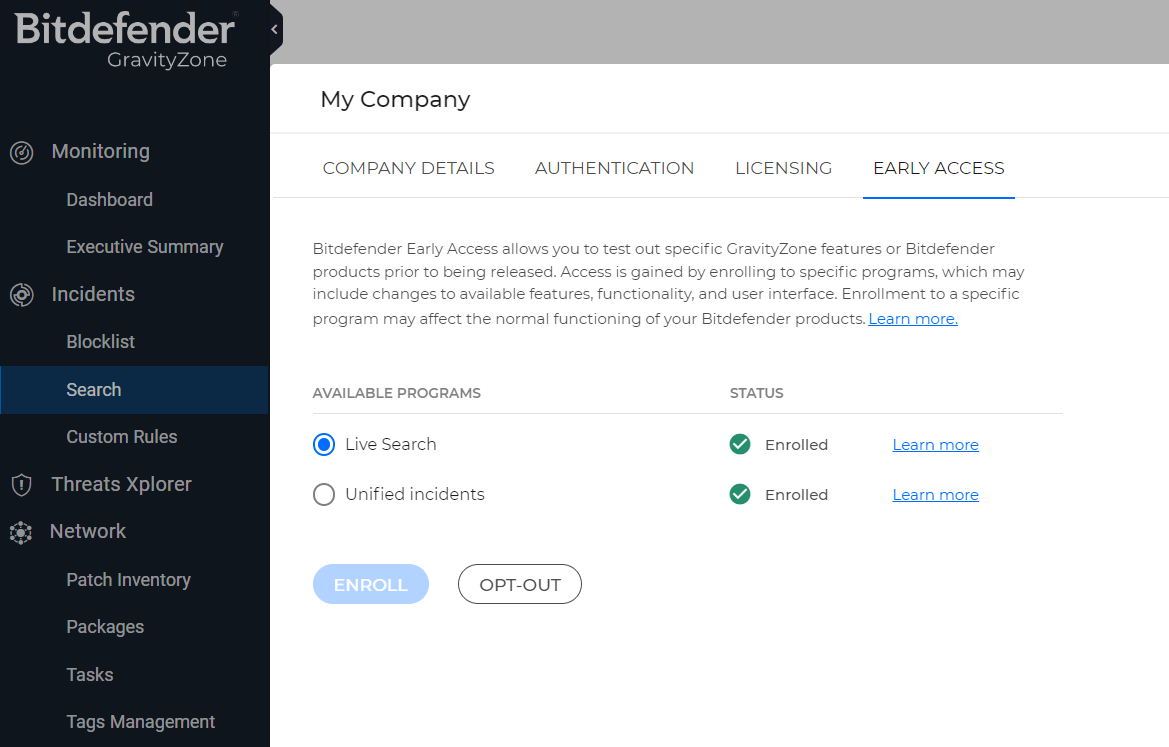
To enable Live Search - Log in to GravityZone. Click on your profile on the upper right side of the screen. From the drop-down menu, select My Company. Go to the Early Access tab. Select one of the programs available on the list. Click the Enroll below the table. Select Enroll to confirm. Your company will gain access to all the features, functionality, and interface changes included in the program.
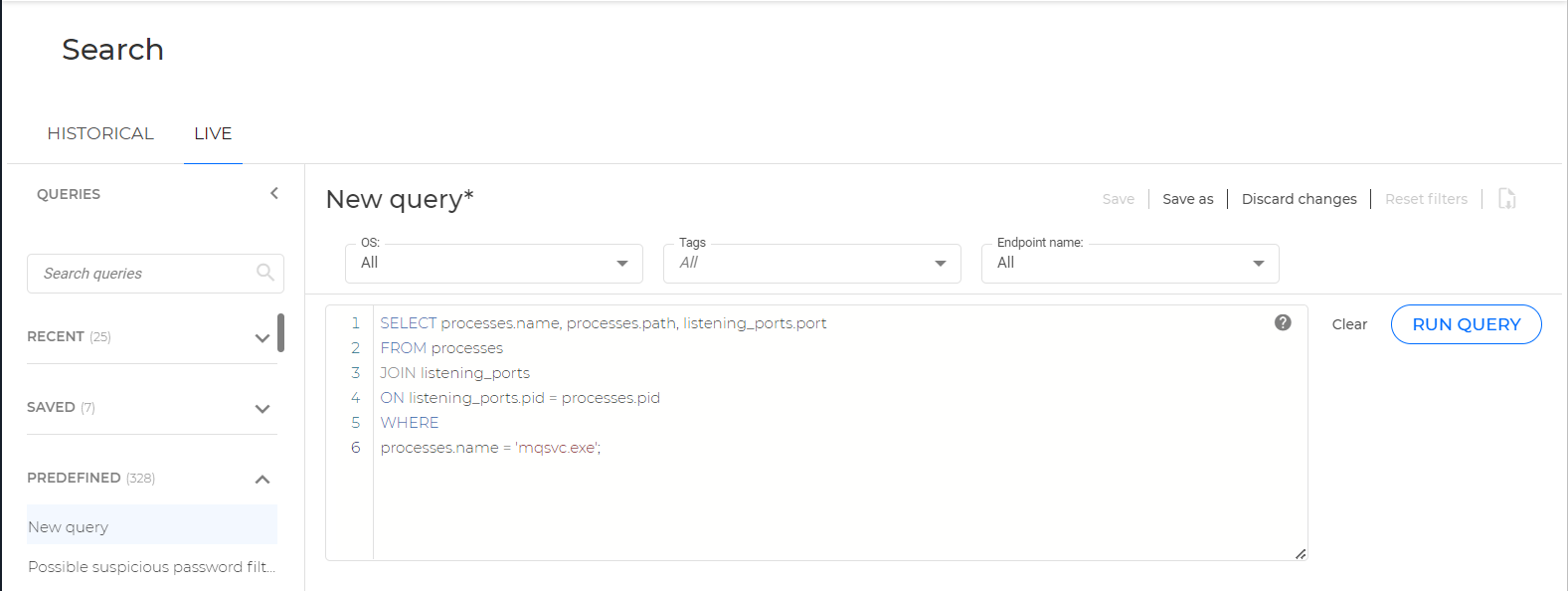
To locate all running instances of mqsvc.exe, use the following query:
SELECT processes.name, processes.path, listening_ports.port
FROM processes
JOIN listening_ports
ON listening_ports.pid = processes.pid
WHERE
processes.name = 'mqsvc.exe';
Actively monitor the infrastructure for potential exploitation attempts and respond accordingly. We strongly recommend implementing detection and response capabilities to detect any suspicious activity on the network and minimize the dwell time of adversaries. Bitdefender GravityZone XDR sensors detect suspicious activity and alert security teams to lateral movement attempts or the establishment of an external connection by the threat actor. This technology can be augmented by good security operations, either in-house or through a managed service like Bitdefender MDR.
For the latest information on vulnerabilities such as this one, subscribe to Business Insights.







