Ransomware – where an attacker steals or freezes an organizations’ computer systems or data and demands a ransom payment to restore access to it – is one of the fastest-growing and most prevalent cybersecurity threats facing businesses today.
The US Treasury’s Financial Crimes Enforcement Network, or FinCEN, reported that more than $590 million in ransomware payments were made during the first half of 2021 alone, and that the top 10 hacking groups have trafficked approximately $5.2 billion worth of ransomware payments in Bitcoin over the past three years. As staggering as those numbers are, they likely underestimate the true scope of the threat, as many ransomware victims never report the crime to authorities or publicly admit to paying the ransom, and it doesn’t account for ransoms paid via other cryptocurrencies.
Although ransomware attacks only began dominating headlines in the past few years, such as seen during the Colonial Pipeline attack or more recently, the ransomware gang that has threatened to overthrow the Costa Rican government, the threat has actually been around much longer. The method of attack and the techniques used have evolved over time, but the incredible damage ransomware attacks can cause to organizations and individuals alike remains the same.
To understand how to better protect against ransomware attacks, we must first look at where we came from.
Ransomware’s earliest ancestor
The earliest known ransomware attack can be traced to 1989, when a Harvard professor named Dr. Joseph L. Popp distributed through the mail 20,000 floppy disks infected with a Trojan malware. After installation, the malware modified a machine’s AUTOEXEC.BAT file and, after 90 boots, encrypted the names of the files on the disk. To decrypt the files, users had to send $189 to a P.O. box in Panama. Ironically, the professor was not a computer scientist or programmer, but an evolutionary biologist involved in AIDS research who claimed that he planned to donate the profits to AIDS educational programs.
Dr. Popp was quickly caught, and ransomware remained a relatively rare threat until the Internet age, which enabled ransomware to become widespread.
Adapting to a new environment
As more organizations and individuals came online, early cybercriminals were able to spread ransomware to more victims, but their methods had a fatal flaw. They used symmetric cryptography, meaning that the encryption and decryption keys were the same and could be extracted from the Trojans themselves. As a result, cybersecurity firms were able to develop universal decryption tools soon after infections were discovered. This wasn’t ideal for the attackers, who quickly realized they needed to make sure each victim was unique so that data could not be recovered until after the ransom was paid.
Much like we often see in nature, as the environment changed, the ransomware species evolved. The next phase in the evolution of ransomware introduced asymmetric cryptography, where an attacker generates a key pair. A public key is stored in the cryptovirus, while the attacker keeps a private key. Once the computer is infected the virus generates a new, symmetric key and uses it to encrypt all files on its disk. The newly generated key gets locked inside an encrypted archive and is removed from the victim’s machine.
After the ransom is paid, the victim must send the encrypted archive to the attacker, who uses the private key to open it, extract the session key and send it back to the victim so they can decrypt their files. In that way, each infected machine requires a unique key and even the attacker cannot decrypt the files without the session key. One victim’s unlock key won’t work for any other victims, and the private key is never shared with the victims. This evolution is now the foundation of every cryptovirus.
The next mutation
With the introduction of asymmetric cryptography, ransomware became much more difficult for victims to remove, resulting in more victims deciding to pay the ransom. However, attackers still needed a more efficient distribution system to spread their viruses. Up until this point, attackers typically relied on distribution through spam emails or phishing attacks that managed to infect single users, not entire organizations. This changed in 2017 with the emergence of the WannaCry worm.
WannaCry still infiltrated an organization through a phishing attack, but once inside it was able to quickly spread through entire networks using SMB vulnerability. This exploit, called EternalBlue, allowed ransomware to spread rapidly through a network without any further action needed from the user beyond the initial infection. It’s estimated that around 200,000 computers were infected by WannaCry across 150 countries. Later, the same exploit was weaponized in the NotPetya and BadRabbit cyberattacks, as well as the Retefe Banking Trojan.
The rise of Ransomware as a Service (RaaS)
Attackers now had effective ways to force victims to pay the ransom and the means to quickly spread their infections far and wide once a network was breached. Cybercriminal groups began producing exploit kits that hackers could purchase on the Dark Web. Those hackers would conduct phishing campaigns with the ransomware buried in a malicious file and reap the rewards of anyone who downloaded the file.
However, this business model turned out to be not very effective. Anti-phishing, antivirus, malware detection, and spam filters were able to stop these kind of ransomware attacks at various points in the attack chain. So, ransomware evolved again.
RaaS models evolve
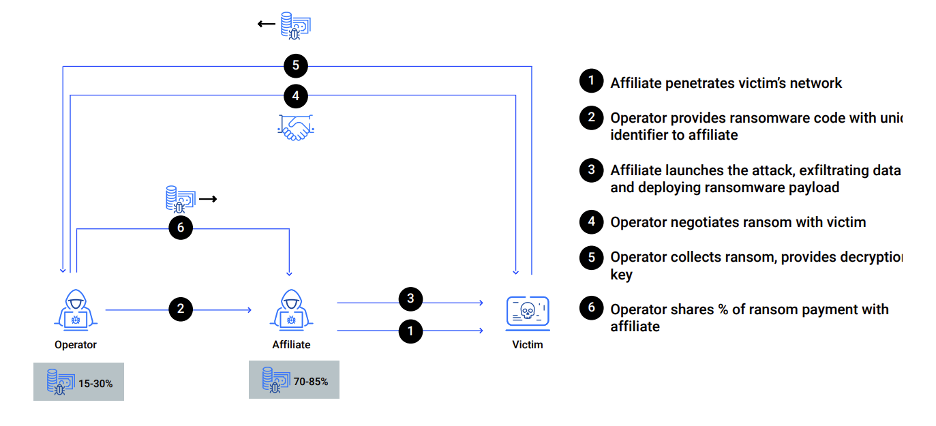
Today, rather than selling their exploit kits and allowing bad actors to use them freely, ransomware groups decided to privatize their most effective strains of malware, license it to affiliates, and split the profits. It’s important to note that RaaS today is not a simple subscription model as it is often described. Rather, ransomware operators develop the malware and run the infrastructure. Their affiliates are not random hackers on Dark Web forums, but more like self-employed contractors who are experts in compromising networks.
After successful breach and deployment, the ransomware operators negotiate and collect the ransom, then distribute the affiliates’ shares. Each part of the operation is an expert with a specialized skill. The affiliates own the access to the networks and receive the largest share of the profit – often up to 80% - 90%. While ransomware operators lead negotiations and get all the media credit for successful attacks, the power today has shifted from those who control the ransomware code to those who control access to the networks.
Understanding this shift in the power dynamic is critical for understanding the anatomy of a modern ransomware attack.
Previously, attacks were opportunistic and utilized worm-like behavior (WannaCry), focusing on the most direct route to monetization. Under today’s profit-sharing model, threat actors have adopted tactics, techniques, and procedures from advanced persistent threat (APT) groups, with a focus on maximizing damage and pressure, not speed. This enables today’s ransomware groups to command the multimillion dollar ransoms we see in headlines. They spend weeks or months preparing for the execution of an attack.
Simple encryption of random data is no longer enough – double or triple extortion is becoming standard practice. A ransomware attack can be combined with data exfiltration (for blackmailing purposes), denial of service attacks, or harassment of executives, partners, and customers. Additionally, ransomware groups’ better understanding of business and corporate financials is playing an important role during the extortion phase. Threat actors often understand the impact of their actions, know which information is most valuable, are familiar with incident response procedures, and understand their victims’ cyber insurance coverage. Before a ransomware payload is delivered, threat actors locate and destroy all available backups.
How to defend against modern ransomware attacks
With such sophisticated adversaries today, how can organizations defend against modern ransomware attacks? The best protection is a defense-in-depth architecture. Organizations should start by reducing the attack surface and employ automated prevention controls, which can prevent most security incidents. For the remaining incidents, they must rely on security operations, enhanced with great detection and response tools.
Strong cyber resiliency and an effective defense against modern ransomware requires a thorough understanding of the adversary, a well-planned security strategy, and the right cybersecurity tools. To learn more about the evolution of RaaS, the emergence of the current profit-sharing model, and why it is such a threat, watch this Bitdefender webinar on the Top 10 Myths and Misconceptions of Ransomware . To gain practical advice for how to protect your organization against ransomware attacks and build a defense-in-depth architecture with the Bitdefender GravityZone Platform, read our ransomware technical white paper.
Ransomware will continue to evolve in response to its environment and the market forces that impact financial payouts. Security professionals should not expect it to become extinct anytime soon. But we can evolve our own strategies and adopt multiple layers of defenses to make our organizations more resilient and prevent them from falling victim to a ransomware attack.
Watch the webinar: Top 10 Myths and Misconceptions about Ransomware
Read our Ransomware Technical White Paper







